How it works

Step 1 here ( or any header about how it works)
Step 1
“As a leading Enterprise Systems Integrator for Information Security and Internet Gateway solutions in Malaysia, we partnered with Invisiron to deliver a next-generation cyber defence platform that is proactive, robust and most importantly invisible to intruders for our government clients.
Step 2 here ( or any header about how it works)
Step 2
“As a leading Enterprise Systems Integrator for Information Security and Internet Gateway solutions in Malaysia, we partnered with Invisiron to deliver a next-generation cyber defence platform that is proactive, robust and most importantly invisible to intruders for our government clients.


Step 3 here ( or any header about how it works)
Step 3
“As a leading Enterprise Systems Integrator for Information Security and Internet Gateway solutions in Malaysia, we partnered with Invisiron to deliver a next-generation cyber defence platform that is proactive, robust and most importantly invisible to intruders for our government clients.

Step 1
“As a leading Enterprise Systems Integrator for Information Security and Internet Gateway solutions in Malaysia, we partnered with Invisiron to deliver a next-generation cyber defence platform that is proactive, robust and most importantly invisible to intruders for our government clients.

Step 2
“As a leading Enterprise Systems Integrator for Information Security and Internet Gateway solutions in Malaysia, we partnered with Invisiron to deliver a next-generation cyber defence platform that is proactive, robust and most importantly invisible to intruders for our government clients.

Step 3
“As a leading Enterprise Systems Integrator for Information Security and Internet Gateway solutions in Malaysia, we partnered with Invisiron to deliver a next-generation cyber defence platform that is proactive, robust and most importantly invisible to intruders for our government clients.
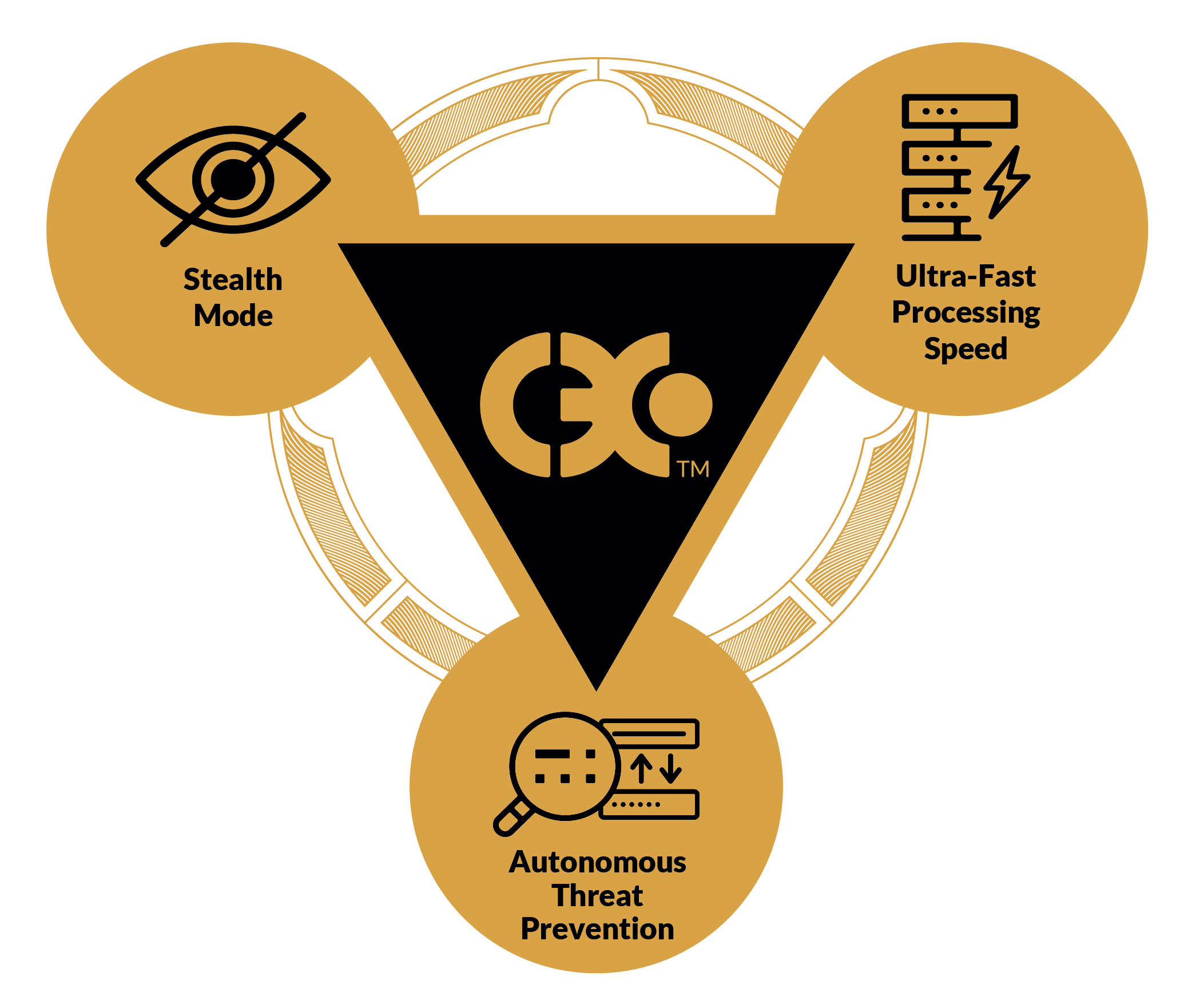
At the core of Invisiron® is C3X™ which features three mission-critical technologies.
Invisible Stealth Mode
Ultra Fast In-Line Packet Processing Speed
Autonomous Threat Prevention
The Invisiron® Cyber Defence device operates in stealth mode, without any IP addresses or Media Access Control (MAC) addresses. This renders it invisible to cyber criminals when deployed. Hackers attempting to penetrate the network will not be able to detect the presence of an Invisiron® device.
Network packets are processed at near line rate without degrading the Internet bandwidth.
The Invisiron Cyber Defence Platform operates fully autonomous with no user intervention needed. Threats are detected and mitigated fully automatically and in real-time.

At the core of Invisiron® is C3X™ which features three mission-critical technologies.
Invisible Stealth Mode
The Invisiron® Cyber Defence device operates in stealth mode, without any IP addresses or Media Access Control (MAC) addresses. This renders it invisible to cyber criminals when deployed. Hackers attempting to penetrate the network will not be able to detect the presence of an Invisiron® device.
Ultra Fast In-Line Packet Processing Speed
Network packets are processed at near line rate without degrading the Internet bandwidth.
Autonomous Threat Prevention
The Invisiron Cyber Defence Platform operates fully autonomous with no user intervention needed. Threats are detected and mitigated fully automatically and in real-time.






